Introduction
1Password requires account holders to deploy an independent SCIM Bridge to support User data and provisioning via API. Learn more about the setup requirements and deployment process in 1Password Support. An Identity Provider (IDP) is not required to configure this integration, but note that the SCIM Bridge setup may vary for connection with different IDPs. Your SCIM Bridge must be fully configured for this integration. You can check the status of your SCIM bridge atyour-scim-bridge-url/app/status.
Enable 1Password User Provisioning
Log in to your 1Password dashboard
Log in to your 1Password account with your Administrator credentials.
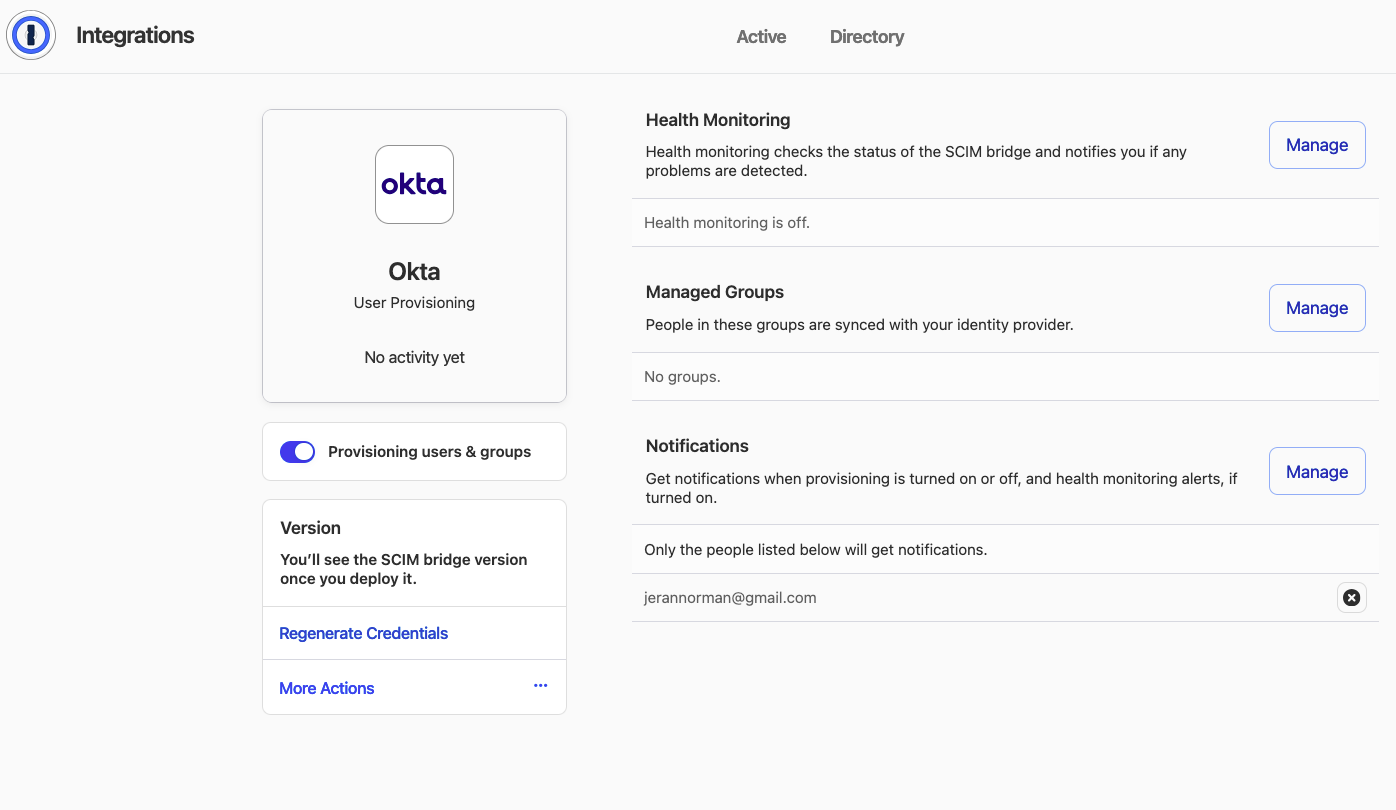
Enable User Provisioning
Navigate to Integrations, and select your listed Identity Provider to proceed. If you do not wish to connect to an IDP, select Okta to be used as the default.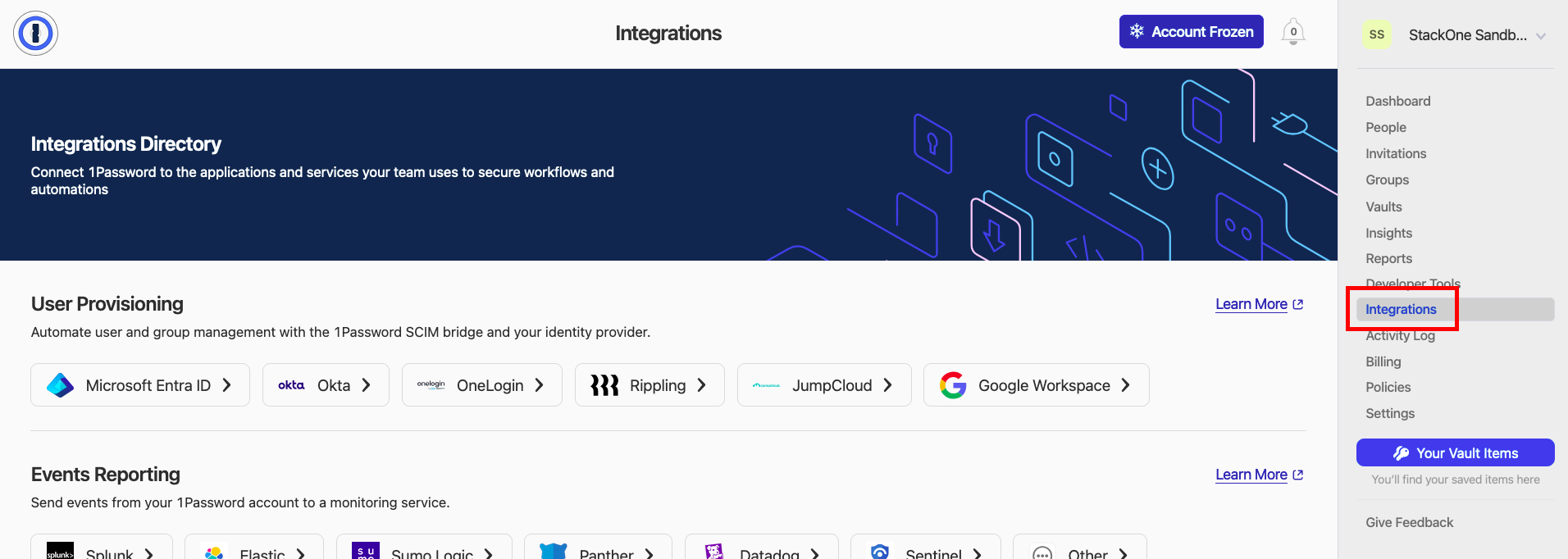

Set up User Provisioning
Based on how your SCIM Bridge will be deployed, select the listed deployment method, then click the Next button.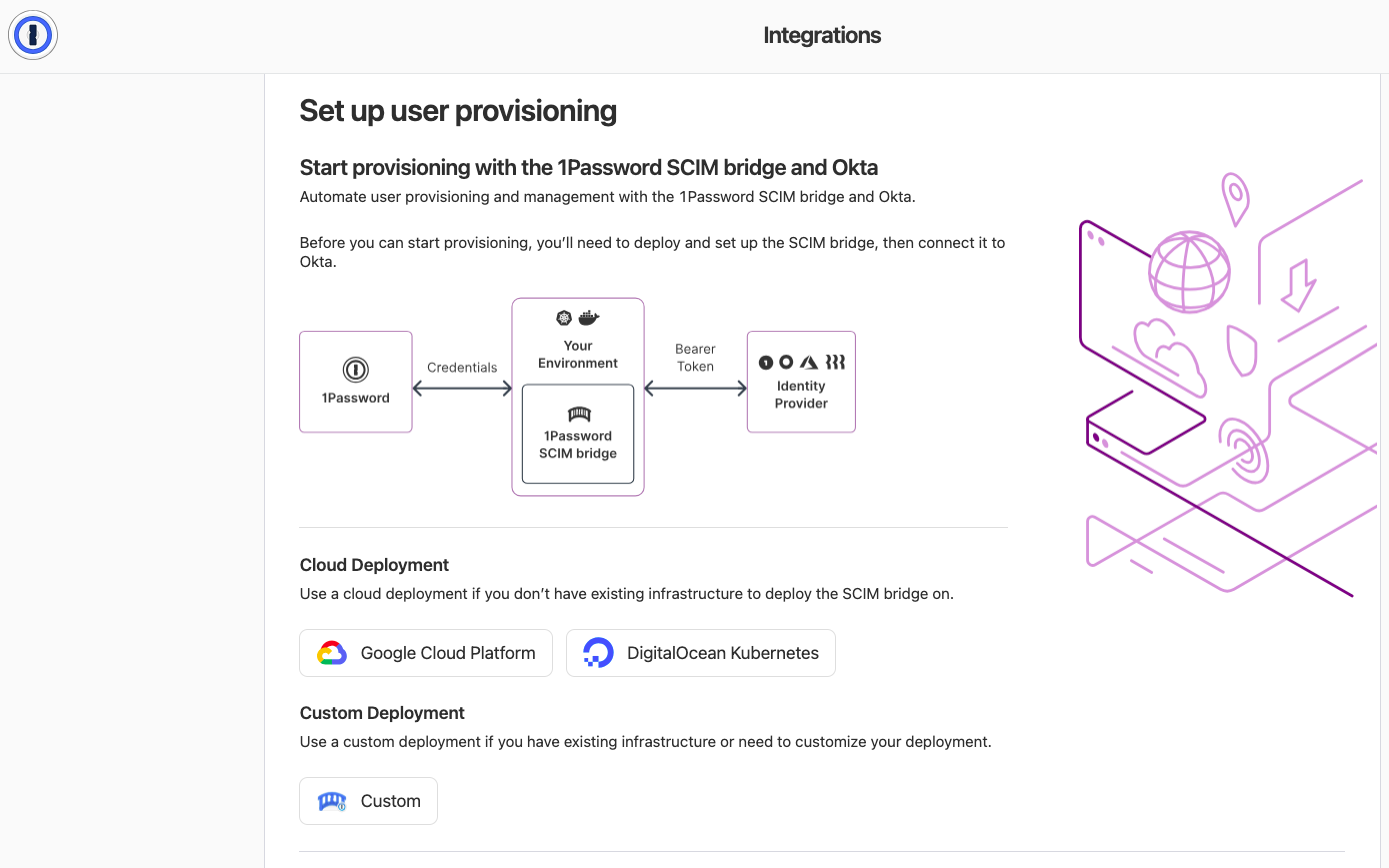

Save Credentials
Download and save your scimsession file securely, which will be used when deploying your SCIM Bridge to connect with 1Password.Download and store your bearer token securely, which both an IDP and this integration will use to connect to the SCIM Bridge.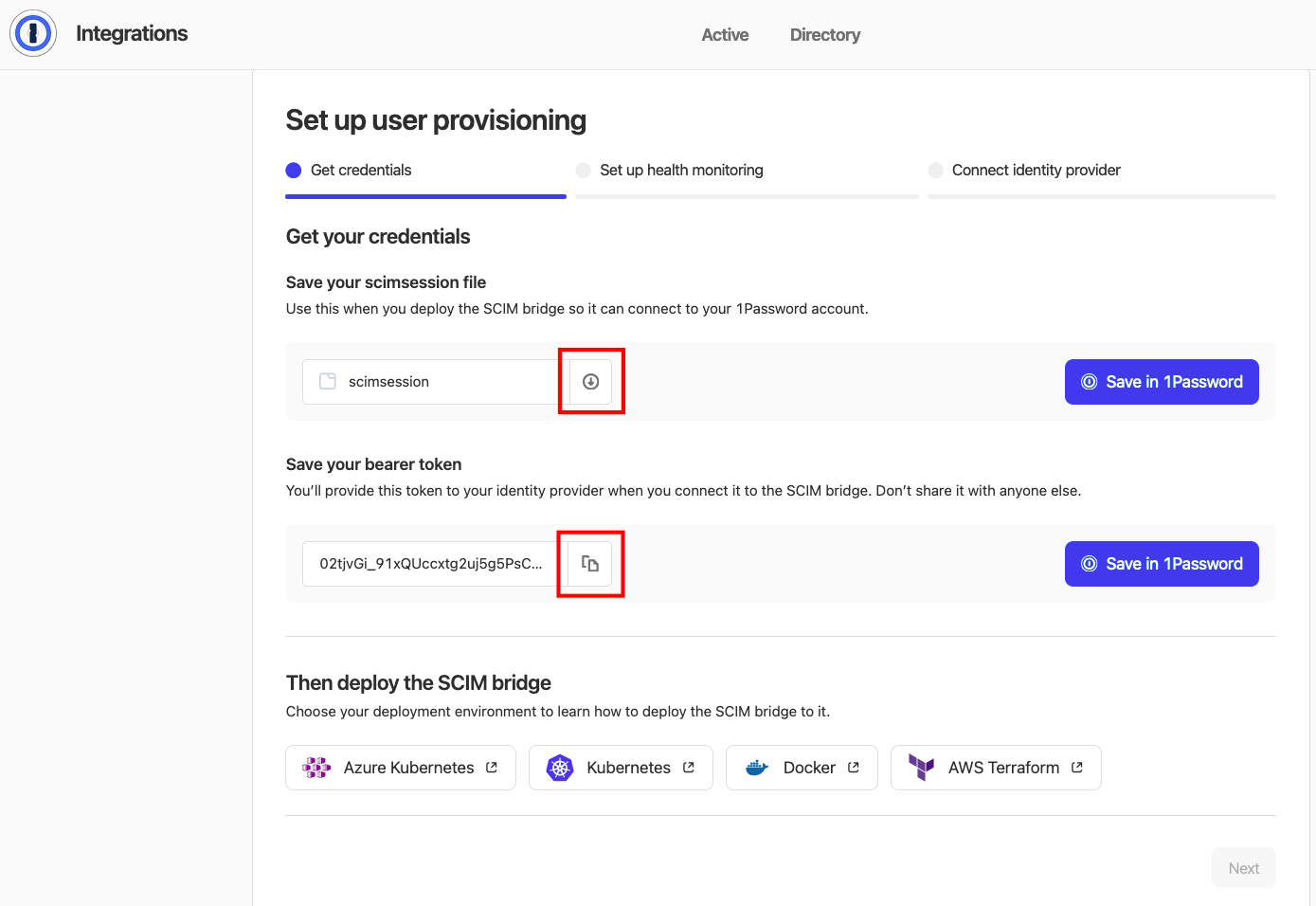

(optional) Set up Health Monitoring
1Password offers an optional alert system to notify you connection issues with your SCIM Bridge.To set up, enable “Turn on health monitoring” and enter the publicly-addressable URL for your SCIM Bridge deployment.Click the Next button to proceed.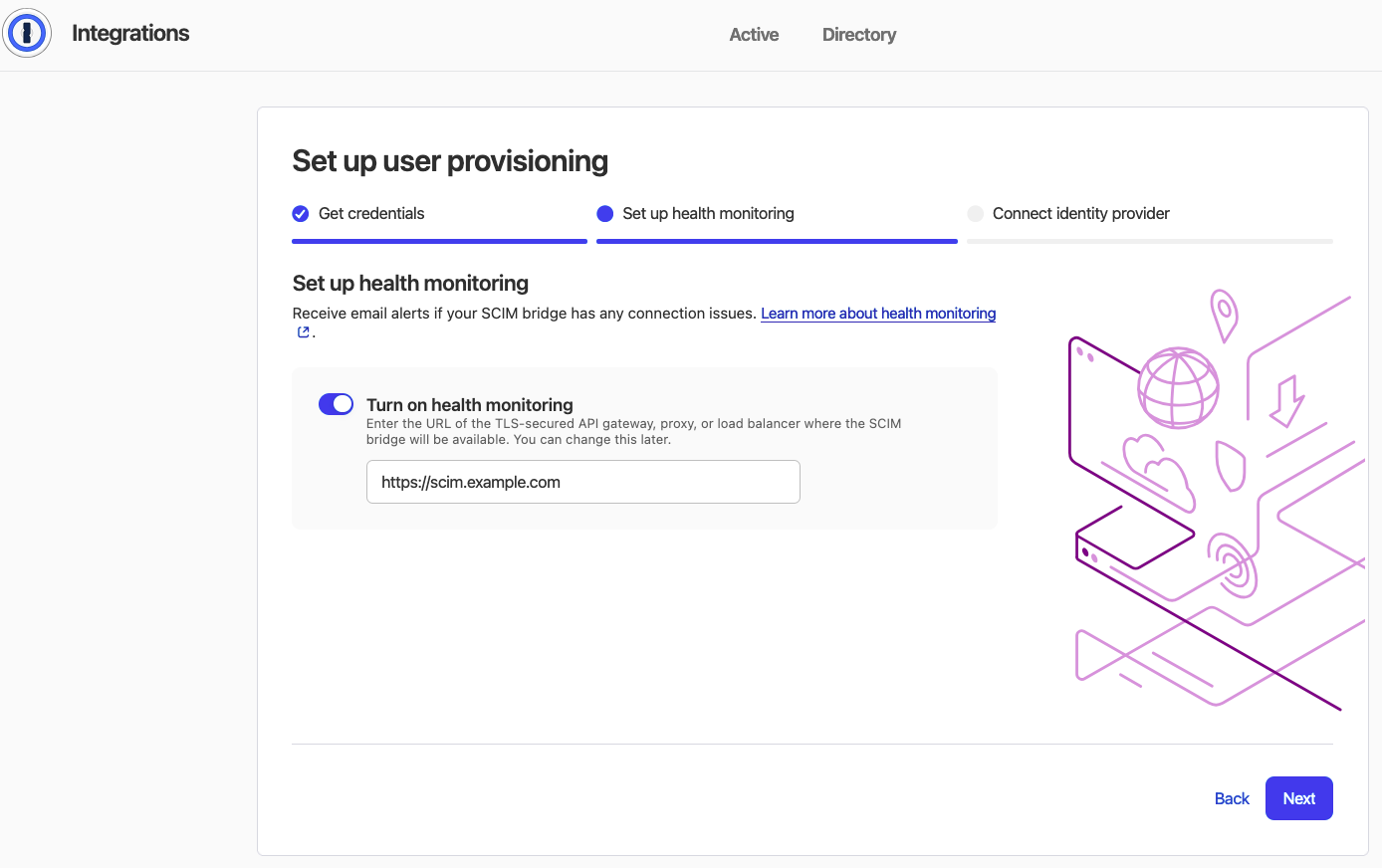

(optional) Connect your IDP to the SCIM Bridge
If you wish to connect an IDP to your SCIM Bridge, click the tile for your IDP to view configuration instructions.Click the “View details” button to open the new User Provisioning configuration profile.
Deploy 1Password SCIM Bridge
Set up your 1Password SCIM Bridge
See 1Password’s official SCIM Bridge deployment examples repo for specific setup instructions across different deployment options.This will require the scimsession file generated from enabling User Provision in your 1Password account.Note the publicly-addressable URL (example:
https://op-scim.mydomain.org) of this deployment, as it is required for establishing this connection.Connecting with StackOne
Enter Credentials
Upon reaching the Link Account page, enter your credentials from the previous steps: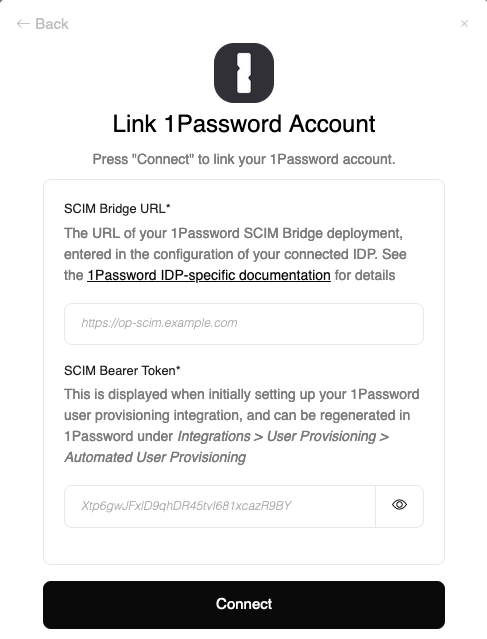
- SCIM Bridge URL: the publicly-addressable URL of your SCIM Bridge deployment. If you have an IDP connected, this will be the same URL entered in the IDP’s 1Password configuration.
- SCIM Bearer Token: the bearer token displayed when initially enabling User Provisioning in 1Password

Congratulations, you’re all set! If you face any issues with the steps mentioned above, please contact us by emailing integrations@stackone.com. We’re always here to assist you!
Available data
This integration has the following IAM Resources available from the provider:- Users
- Groups